What is Penetration Testing?
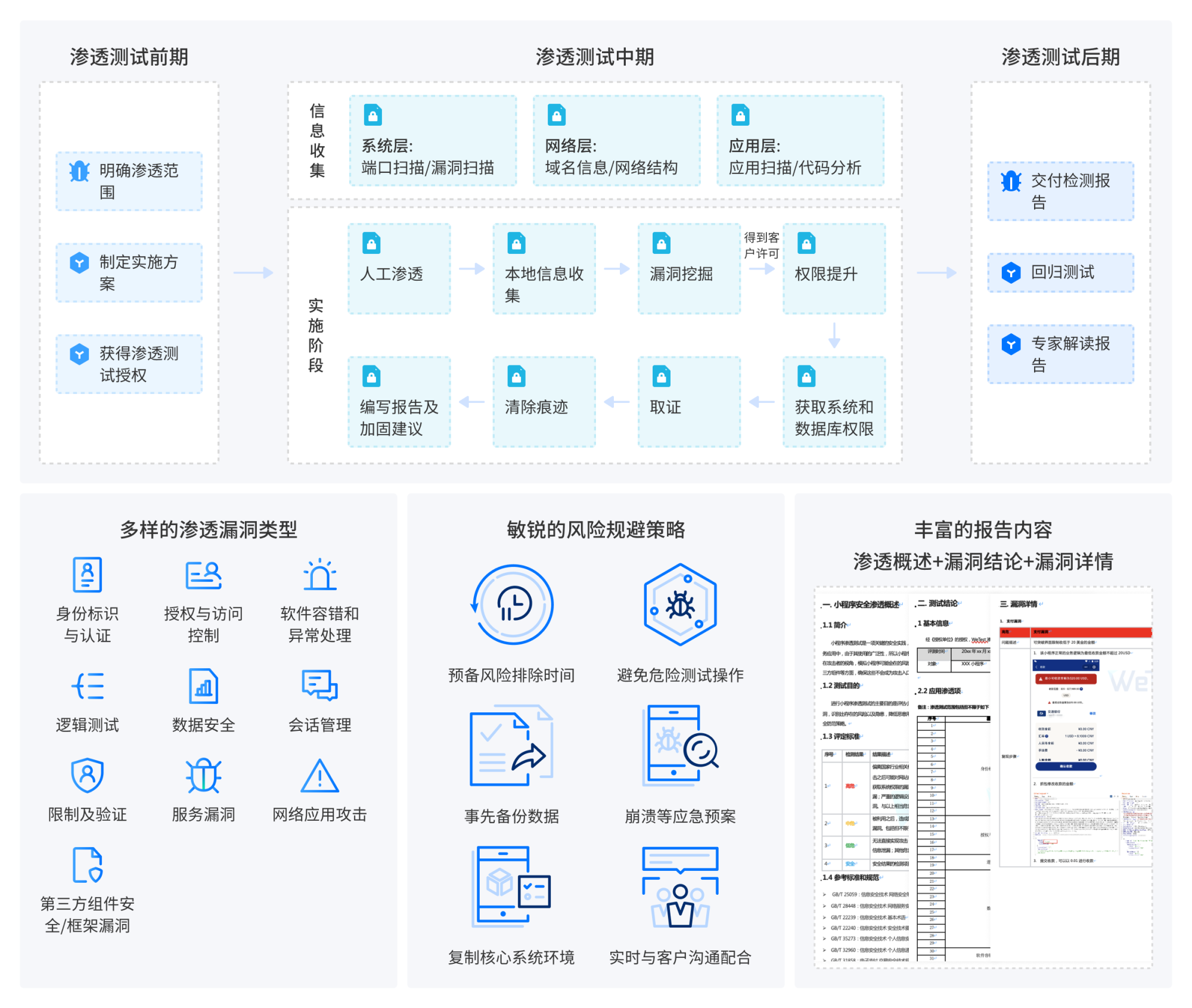
Penetration testing services are expert-level security testing services provided to WeTest clients. These services conduct comprehensive security assessments throughout the entire lifecycle of application data. Approaching from both a hacker's mindset and a debugging perspective, the testing covers multiple aspects, including application security, data security, business logic security, transmission protocol security, encryption algorithm security, privilege escalation, injection attacks, and interface vulnerabilities. Through both static and dynamic manual penetration testing, the service identifies potential security risks related to data usage, user data input, storage and processing, network transmission, and the operating system environment in which the application runs.
The Difference Between Mini Program Penetration Testing and Scanning
Scanning primarily relies on automated tools, aiming to cover a wide range of authoritative vulnerability databases to identify known security issues. In contrast, penetration testing focuses more on simulating real-world hacker attacks. Conducted by professional teams using a combination of manual and automated methods, it involves in-depth analysis of various functions and components of the mini program. This approach helps uncover unknown risks and identify complex and customized attack techniques.

Learn More About Penetration Testing Services
WeTest supports penetration testing for a variety of product types, including mini programs, mobile apps, and web applications. Testing service items can be flexibly combined based on client requirements.
Contact Us Now

15+
Total Number of Industries Served
1000+
Total Number of Mini Programs Served
10000+
Number of Penetration Testing Cases
99%+
High-Risk Vulnerability Detection Rate per Client
Business Pain Points
1. Lack of Security Expertise Among Internal Technical Staff: There is insufficient long-term experience and understanding of common system and business vulnerabilities within the industry, making it difficult for internal teams to conduct comprehensive and systematic penetration testing on their own.
2. High Cost of Security Tools and Learning: With the rise of black and grey market threats, attack techniques are constantly evolving. If internal developers are required to learn and adapt immediately, it can result in significant time and financial costs.
3. In-House Development Leading to Business Blind Spots: While internal staff may be highly familiar with the mini program system and their own business processes, this deep familiarity can lead to inherent biases and blind spots in vulnerability detection and penetration testing.
Business Outcomes
1. After a comprehensive security assessment, the WeTest penetration testing team rated the client's online shopping mini program as high-risk.
A total of 8 security risks were identified during testing: 2 high-risk, 5 medium-risk, and 1 low-risk. For example, the order interface was vulnerable to abuse (e.g., coupon or discount exploitation), and it was possible to bypass front-end restrictions to add excessive items to the shopping cart. WeTest experts provided corresponding solutions for each vulnerability and offered one-on-one video sessions to explain the remediation plans in detail.


